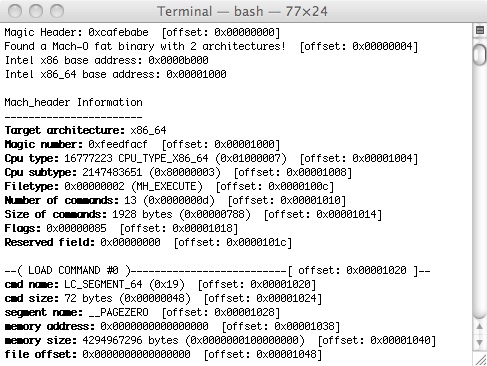
For a long time I have been annoyed by the information displayed by otool -l because it mixes hexadecimal with decimal information. For example, offsets are displayed in decimal and relative to the CPU architecture in the fat binary. So I had to convert and calculate things by hand everytime I wanted to peek or modify something at the hex editor. HTE allows to see this information and even edit it, but it doesn’t support fat binaries (and I have to start it under iTerm to support the keyboard shortcuts – I didn’t want to waste time researching to get it to work with Terminal.app).
Then a reader sent me a new protection (a packer) and I started having some fun with it and again I needed a tool to display all the offsets so I could try some crazy approach to the target. Since I’m on short vacations from the MBA and I miss the adrenalin of having all my time occupied I rewrote otool -l option in Perl (yeah lots of free time to reinvent the wheel and learn something ehehheh). So ptool.pl is born. It will process x86, x86_64 and PPC binaries and dump all the information from the mach-o header, together with the correct offset location inside the binary. This way it is very easy to navigate inside the hex editor.
I’m thinking about converting it into a full mach-o editor using Perl+ncurses. I would love to have a nice GUI in Cocoa but I don’t have time to mess with Objective-C for now (and I suck at object-oriented languages, more than other languages). I’m thinking too to modify otool and fix that damn display and add some other features, like disassembling any chosen offset of the binary file (it’s helpful some times and it would remove the need for an external disassembler like this one – my idea is to integrate it into otool or use otool own disassembler). It will depend on time and motivation. I can’t reverse the protection if I take all the time to write and fix tools.
So here it is version 1.0 of ptool:
ptool1.0.zip
(SHA1(ptool1.0.zip)= be754c87fcfbd4ee43d47aeba197a1f20c81e296)
If you find any bug or have any suggestion feel free to leave a comment or email.
Btw, the target protection is called VLOK and is available here (updates are protected so you can use them as targets). I’m not thinking about publishing full details and code but a general analysis and description of the tricks and its design. I still believe in full disclosure but the legal and business sides are more complex and the world isn’t always as we want (all that and a 500 pages book on Business Ethics that I had to read for an exam). And what’s the fun of having everything cooked for you? If you want to learn you have to think and practice!
Have fun!
fG!
Update:
If you want to recompile otool you need to follow the gdb guide and then do the following:
- Package name is cctools
- First use darwinbuild -nochroot cctools
- Compilation should fail with some include errors
- Edit the following files:
Build10C540/BuildRoot/SourceCache/cctools/cctools-750/Makefile, search for -DTRIE_SUPPORT and remove it (you can leave echo “”)
Build10C540/BuildRoot/SourceCache/cctools/cctools-750/misc/Makefile and remove the options for LTO and TRIE
Build10C540/BuildRoot/SourceCache/cctools/cctools-750/libstuff/Makefile and remove the options for LTO - Recompile again, this time with darwinbuild -nochroot -nosource cctools
- Wait and enjoy the recompiled otool. Now you can modify its source code 😃.
- otool seems to work fine without those includes so hell with them!