Today I am finally releasing one of the EFI reversing tools I built when I was working on the SCBO post.
Yesterday there were some tweets about IDA improving its support for EFI binaries (although I’m not sure it’s the same thing as in here) so I decided to finally release this one.
You can find the source code https://github.com/gdbinit/EFISwissKnife.
Tested with IDA 6.9 and IDA 6.95 OS X versions, might work in Windows with just paths modification.
It is based on Snare’s work, https://github.com/snare/ida-efiutils. Since I hate Python I rewrote it in C and added some extra features.
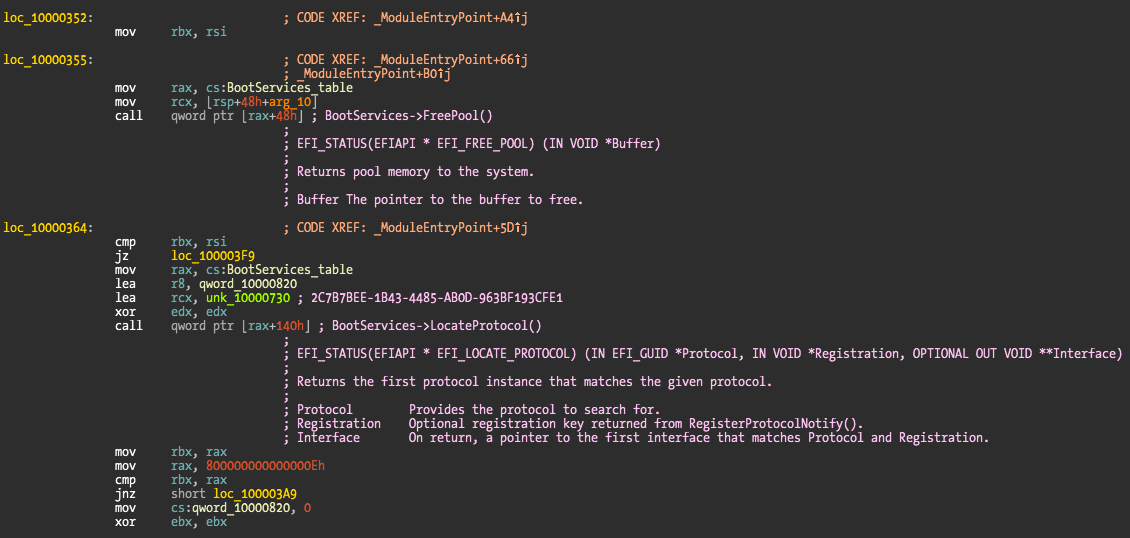
I opted for not renaming the function pointer calls to names as Snare does but instead just leave everything as a comment.
One of the features I added is to generate statistics about the Protocols and Boot/RunTime services. This way you can have a quick idea of what the target binary is using in terms of EFI services and Protocols.
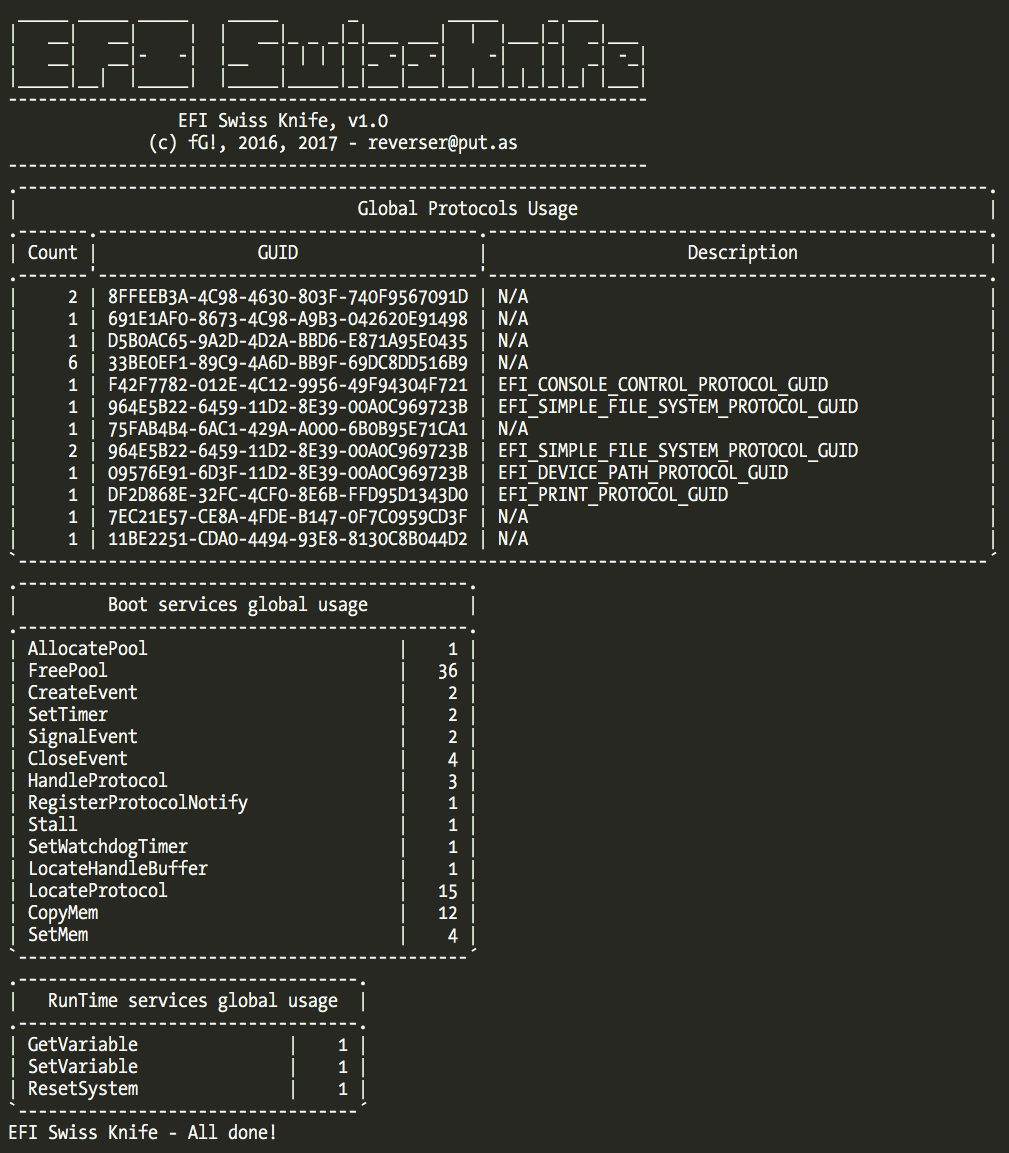
It also features a batch mode that you can use with IDA own batch mode to gather statistics from all the binaries in a firmware dump for example. It also has the ability to write to a database so you can easily query information.
Please check the README file for extra information and definitely the code. Feel free to submit updates, in particular to the EFI GUIDs database.
Have fun,
fG!